Access
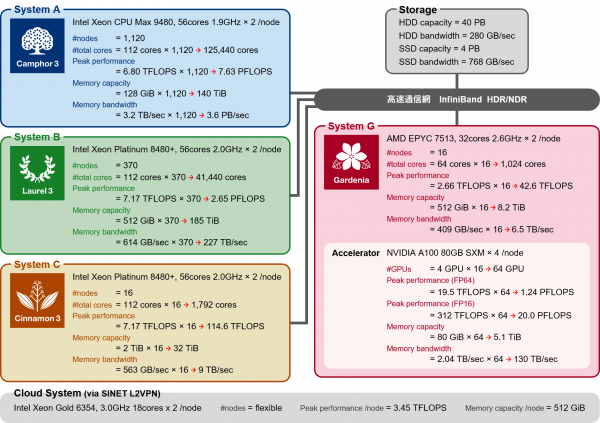
Supercomputer systems of Kyoto University consist of five types of systems and storage. For details, please refer to Institute for Information Management and Communication, Kyoto University.
Login to the supercomputer is limited to SSH (Secure SHell) key authentication. You can login by generating a key pair and registering a public key from User Portal. You cannot log in with a password, so you must first register your public key.
The flow of login is shown in the figure below. For specific instructions, please refer to Access.

The host name for each system is as follows. Please log in with the login name (user ID) provided on the approval notice for supercomputer use and the private key corresponding to the public key registered on the User Portal.
| System Name | Host Name | Notes |
|---|---|---|
| SysA | camphor.kudpc.kyoto-u.ac.jp | Consists of two login nodes. |
| SysB/Cloud | laurel.kudpc.kyoto-u.ac.jp | Consists of three login nodes. |
| SysC | cinnamon.kudpc.kyoto-u.ac.jp | Consists of three login nodes. |
| SysG | gardenia.kudpc.kyoto-u.ac.jp | Consists of two login nodes. |
| File Transfer Server | hpcfs.kudpc.kyoto-u.ac.jp | Consists of two servers. Dedicated SFTP and RSYNC servers with no time limit. |
The fingerprint for each system is as follows.Please use it to confirm the fingerprint that is displayed when you first login to the system via SSH.
| System | Method | fingerprint |
|---|---|---|
| SysA | RSA | SHA256: o/Ef0rC2uksvUax14XF6R9c3WHWypaSDfDjDJ0lkreQ |
| '' | ED25519 | SHA256: yoBITHVW+ENaAAAlW+ZZDCUBnCNFEhBDsnWHjMHFKx0 |
| '' | ECDSA | SHA256: 8j+LvvPha40b2ZwrN3J7s3fyzD+SxHU67/5MwKAUqVU |
| SysB/SysC/Cloud | RSA | SHA256: c3KPtVlPbgGW+jFM8VdGd4yob4HX/VPH7nR26JHS13M |
| '' | ED25519 | SHA256: jt5nEfylQ+SjG5PUZtKqP1DXk56p+7ugwF8GHx8Nr/Q |
| '' | ECDSA | SHA256: yJN7gkHzsrlRBwvYsTCiQkXnzEkdZmjMZLs9TO8YylU |
| SysG | RSA | SHA256: 7GWj0iRCCMpswAWWyIZC+FMX3xlQVRyFiP9hIUYl3rU |
| '' | ED25519 | SHA256: 8uh/6B14HEz77F1yAq95CyQHLqKqr4DG2Xys7eQr0qk |
| '' | ECDSA | SHA256: PJX5f4jPqjTM4Awpod8fedTEXknIBamdexYK3fAzl6U |
| File Transfer Server | RSA | SHA256: /ZeTSRgrxAo4Et1E9NouKs8xyhc/KAjgRpqaEgf37sM |
| '' | ED25519 | SHA256: v0ABGIXX735Ak2By6zq1IuwPAPwLmJC8IwEhzAlm7ds |
| '' | ECDSA | SHA256: RtD7xSYrSL/F6KZpZcjluDFlQ37CIVD6ij2GhEYOaO0 |
If you do not need the GUI, you can log in with SSH Client
You can also log in with MobaXterm.
FastX, NiceDCV and MobaXterm(Windows Only) can be used.
For file transfer to and from the supercomputer, scp or sftp, which uses SSH function for file transfers are used. SCP is Secure Copy and SFTP is Secure FTP. When transferring files, the private key corresponding to the public key registered in the User Portal must be used.
Please refer to File transfer with SSH for file transfer using SSH client.
There are three supercomputer login nodes in Systems B, C, and Cloud standard, and two in System G. They are operated by DNS round robin for load balancing. If a failure occurs on some of those nodes, login by DNS round robin may fail. Please follow the procedure below to login by specifying individual host names.
| System | Host |
|---|---|
| SysA | camphor31.kudpc.kyoto-u.ac.jp |
| '' | camphor32.kudpc.kyoto-u.ac.jp |
| SysB/クラウド | laurel31.kudpc.kyoto-u.ac.jp |
| '' | laurel32.kudpc.kyoto-u.ac.jp |
| '' | laurel33.kudpc.kyoto-u.ac.jp |
| SysC | cinnamon32.kudpc.kyoto-u.ac.jp |
| '' | cinnamon32.kudpc.kyoto-u.ac.jp |
| '' | cinnamon33.kudpc.kyoto-u.ac.jp |
| SysG | gardenia11.kudpc.kyoto-u.ac.jp |
| '' | gardenia12.kudpc.kyoto-u.ac.jp |
In order to use the supercomputer system, users must strictly manage their own passwords for the user portal and passphrase for the private key for key authentication. When creating a password/passphrase, please make sure that it is a string of characters that cannot be easily guessed by a third party from the account information.
Please refer to the following sites for tips on creating secure and strong passwords/passphrases.
- Create and use strong passwords (Microsoft)
- Password Checker (Microsoft)
- Tips for creating secure passwords on your Mac (Apple)